Jetico Setup Utility V 1.0 PC Software
In the ever-evolving field of digital security, the necessity for effective encryption and data protection measures is vital. Jetico Setup Utility V 1.0 appears as a robust solution, offering customers a complete range of functions to safeguard their critical information. In this post, we will go into the introduction, overview, features, and system requirements of Jetico Setup Utility V 1.0.

Introduction:
Jetico Setup Utility V 1.0 is a cutting-edge program developed to fulfill the severe security needs of current users. Developed by Jetico Inc., a famous brand in the world of data security and encryption, this tool marks a significant milestone in preserving digital assets. The program is built to deliver an easy and user-friendly experience while ensuring top-notch security procedures.
You may also like:: iTubeGo YouTube Downloader 7.1.0 Multilingual x64 PC Software
Overview:
Jetico Setup Utility V 1.0 is a flexible tool that primarily focuses on establishing and managing secure containers for sensitive data. These containers operate as virtual vaults, utilizing powerful encryption methods to keep information safe from unwanted access. The program employs a simple and easy UI, making it accessible to both novice and expert users.
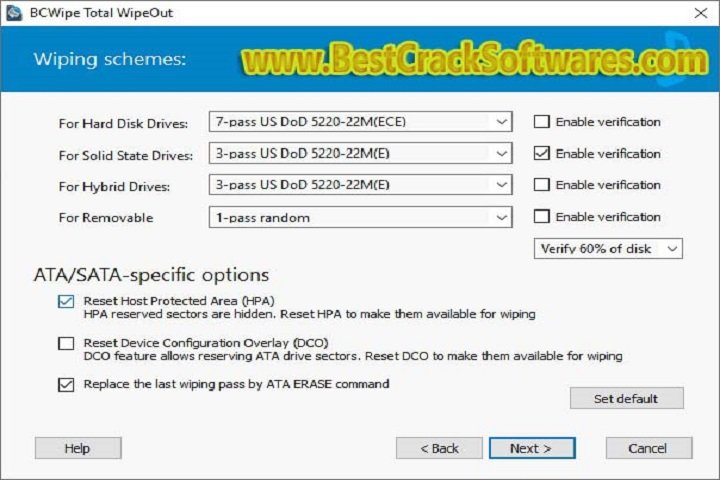
Key Components:
1. Container Creation Wizard:
The program provides an informative wizard that helps users through the process of establishing secure containers. Users may choose the size, encryption techniques, and access credentials for each container, adjusting the security parameters according to their individual needs.
2. Strong encryption techniques:
Jetico Setup Utility V 1.0 implements state-of-the-art encryption techniques, including AES-256, guaranteeing that data saved within the containers stays almost impenetrablei. This degree of encryption is critical for securing sensitive information from potential attackers.
3. Mounting and Dismounting:
The tool allows users to smoothly mount and dismount containers, enabling on-the-fly access to encrypted data. This functionality guarantees that users may access their encrypted information whenever needed, while simultaneously guaranteeing that illegal access is blocked while the container is not in use.
4. Portable Containers:
Jetico Setup Utility V 1.0 introduces the notion of portable containers, enabling users to transport their encrypted data on external disks or storage devices. This flexibility offers a degree of convenience for consumers who require access to their encrypted information on multiple devices.

Features:
1. Multi-Layered Security:
The program contains a multi-layered security strategy, integrating encryption, password protection, and container isolation. This guarantees that even if one layer is hacked, the total security integrity remains maintained.
2. Customizable Encryption Settings:
Users have the freedom to pick from a range of encryption methods and key lengths, allowing them to personalize the level of security based on their unique requirements. This versatility is vital for catering to varying security demands across various businesses.
3. Seamless Integration:
Jetico Setup Utility V 1.0 effortlessly integrates with the user’s workflow, giving quick access to protected containers without disturbing normal activities. This integration is aimed at boosting security without creating inconvenience.
4. Centralized administration:
For businesses working with several containers and users, the program offers centralized administration tools. This includes the ability to create access controls, monitor container utilization, and execute changes throughout the network.
5. Audit Trails and Logging:
To support compliance and forensic investigation, the utility offers extensive audit trail and logging features. This guarantees that administrators can trace access to and alter data within the containers, boosting openness and accountability.
Requirements:
Jetico Setup Utility V 1.0 is designed to be interoperable with a range of platforms, providing extensive accessibility. The following are the critical system requirements for best performance:
1. Operating System:
Windows 10 (32-bit or 64-bit)
Windows 8.1 (32-bit or 64-bit)
Windows 7 SP1 (32-bit or 64-bit) ### 2.
Processor: 1 GHz or faster processor
3. RAM:
1 GB RAM (32-bit) or 2 GB RAM (64-bit)
4. Storage:
50 MB of available hard drive space for installation
5. Additional Requirements:
Internet connection for product activation and updates It is crucial for users to ensure that their systems fulfill these criteria to enjoy the full range of features and functions offered by Jetico Setup Utility V 1.0.
You may also like:: Drive Snap Shot 1.0 Pc Software
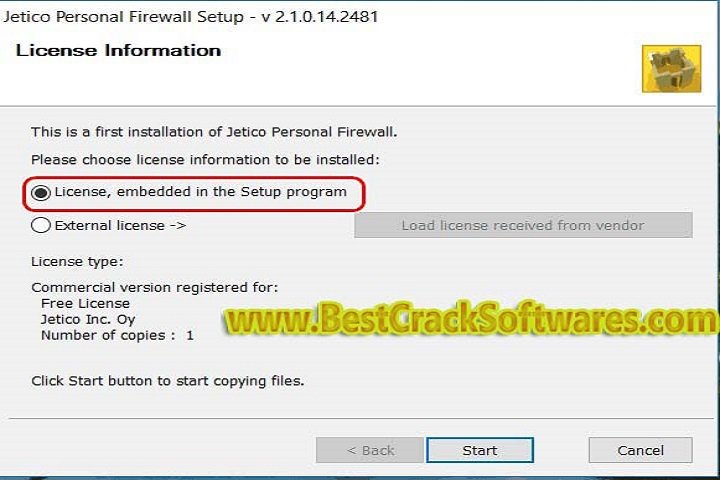
Conclusion:
In conclusion, Jetico Setup Utility V 1.0 serves as a testament to Jetico Inc.’s dedication to offering top-tier security solutions. With its straightforward interface, effective encryption algorithms, and diverse features, the program emerges as a trusted solution for people and enterprises seeking comprehensive data security. By effortlessly integrating security into regular activities and giving customized encryption choices, Jetico Setup Utility V 1.0 is positioned to become a cornerstone in the area of data protection. As the digital world continues to grow, this utility shows itself to be a helpful ally in the continuing war against cyber threats, helping users to preserve their sensitive information with confidence.
Download Link : Mega
Your File Password : BestcrackSoftwares.com
File Version 1.0 & Size : 11.2MB
File type : Compressed / Zip & RAR (Use 7zip or WINRAR to unzip File)
Support OS : All Windows (32-64Bit)
Upload By : Somia Saleem
Virus Status : 100% Safe Scanned By Avast Antivirus



